Towards a model of resilience in decentralised socio-technical infrastructure
Kelsie Nabben
7 July, 2021
“Resilience” is an evolutionary concept in decentralised technology communities.
Resilience was sought via distribution of computing architecture against the threat of war by Paul Baran in the 1960s.[1] It was then sought through cryptographic security of data and privacy through the work of public key cryptographers in the 1970s and 1980s.[2] Resilience then became a political objective, for autonomy from state control or intervention under the cypherpunks in the 1990s.[3] The explicit overlay of political ambition to decentralised technologies introduces challenging dynamic when trying to establish “decentralised” governance. With infrastructure, “no tool is neutral”.[4] Each of these instantiations of resilience coalesced around a conception of the “common good”. In this piece, I explore a framework resilience in decentralised digital infrastructure that challenges makers to consider their subjective version of the “common good”, in terms of the outcomes that their infrastructure produces for those that use it.
These historical breakthroughs in distributed computing and public key cryptography culminated in the invention of Bitcoin in 2008: an architecturally decentralised, cryptographically secure, coordination infrastructure, that also promotes political decentralisation by disintermediating centralised third parties through distributed consensus. Bitcoin has formed the technical and ideological basis of a proliferation of development in decentralised technologies, largely supported by the introduction of economic incentives it enables.[5] Bitcoin helps form a basis for further research into decentralised technologies, as an important object of social enquiry.[6]
Understanding Information Infrastructure
Hanseth and Monterio define information infrastructure as enabling, shared, open, heterogenous, [7]
One way to identify information infrastructures is as:
· enabling a function, shared by a community, and open in terms of users (or permissionless[8]),
· heterogeneous in terms of diverse and encompassing of socio-technical components, including hardware, information, software applications, standards, and people, and connected as ecologies of networks (or interoperable),
· installed base in that they constantly replace themselves on the foundations of previous infrastructure (see “Ship of Theseus”[9]).
Decentralised technologies as socio-technical infrastructure
Decentralised infrastructures are socio-technical systems, consisting of social and technical components, which shape and co-construct one-another.[10] These “composable” systems are comprised of software code, engineers, community members, algorithms, internal policies, external policy subject to the jurisdictions in which they operate, hardware, and networking. They form functional technology stacks and organisations, from protocols, to decentralised applications, to “Decentralised Autonomous Organisations” (DAOs). These multi-scale constructs operate at the individual, organisational (or institutional), and societal levels.[11] These characteristics provide a basis for further enquiry into a socio-technical definition of resilience.
Edwards, et. al. argue that the history of most large-scale infrastructures includes two crucial moments. “One is a gateway phase, discussed above, in which technical, political, legal, and/or social innovations link previously separate, heterogeneous systems to form more powerful and far-reaching networks. The other is a recurring issue of adjustment in which infrastructures adapt to, reshape, or even internalize elements of their environment in the process of growth and entrenchment. These are also the points at which most systems fail to become infrastructures: they cannot successfully link with other systems, adapt to a changed environment, or reshape or internalize environmental factors to grow and consolidate. A principal reason most systems fail is that these critical moments are difficult to anticipate or plan for, and rarely lend themselves to deliberate design”.[12]
This second, crucial phase in large-scale infrastructures of adaptivity can also be referred to as resilience.
Identifying socio-technical resilience
Amir and Tantri define resilience as “adaptability and transformability of a socio-technical system in response to threat or crisis”.[13] In other words, resilience is found in the adaptive capacity of a system, afforded by both social and technical adaptions and transformations, which leads to its ongoing ability to function, towards its said objectives.
Returning to the need to identify our notion of the “common good”, resilience thus centres around the social context and outcomes of our tools, as critical, digital, public infrastructure. One such example could be the privacy and security of people using the infrastructure.[14] Another could be the function the infrastructure performs, such as funding public goods.[15]
In this context, “the art of governing” is the practices of governments and their effects on people, and how people govern themselves.[16] Foucault’s theory of “governmentality” emphasises the governing of people’s conduct through positive means, rather than by the imposition of an external sovereign power that applies the law, in his approach to the study of power.[17] Technologies of power are the resources used to help develop good behaviour, with the idea of creating positive norms and behaviours, while attempting to avoid negative ones. Technologies of self involve the capacity of individuals to control and govern themselves, including restricting their own negative behaviours, while promoting positive behaviours for personal and societal benefit. Technologies of the Market are those which economically incentivise certain behaviours, such as buying behaviour or directing labour. In some ways, this is comparative to blockchain communities, in the social, technical, and cryptoeconomic scales of leverage in governance and resilience.
“Governing” vulnerabilities
The aim of governance is to determine the surface of human actions, towards desirable, said social outcomes that align with the purpose of the participating community. Here, it is the social consequences of infrastructure that matter.[18] Science and Technology studies scholars argue that vulnerability is a relational notion to resilience, by which it can be observed and addressed through governance. [19] To do this, the “vulnerabilities” of various stakeholders in an infrastructure must be considered.
Hommels, et. al define “vulnerabilities” as an emergent and relational properties that pervades everyday life, and are firmly embedded in the context in which they emerge. [20] Vulnerabilities can include environmental factors (“livelihood” vulnerabilities), power structures, or other properties that are co-produced between technical and social factors in technological cultures. Vulnerabilities can also co-exist, compete, and intertwine in multiplicity. When approached as a design problem, “vulnerabilities” can be framed as the violation of an objective, subject to a constraint.[21]
Once vulnerabilities are identified, they can be “governed” to improve adaptive capacity, through various mechanisms, including values systems, community relations, knowledge, and technology.[22] For example, a dam wall in the Netherlands is a technology which governs the population against the threat of flood, as some cities are below sea level.
Governing vulnerabilities surfaces the requirement to identify which stakeholders are responsible and accountable in the system, for example, law, social norms, or algorithms.[23] When addressed, vulnerabilities are sometimes moved in time and space, rather than eradicated.
Towards a framework for observing and governing vulnerabilities, for resilience in decentralised socio-technical infrastructure
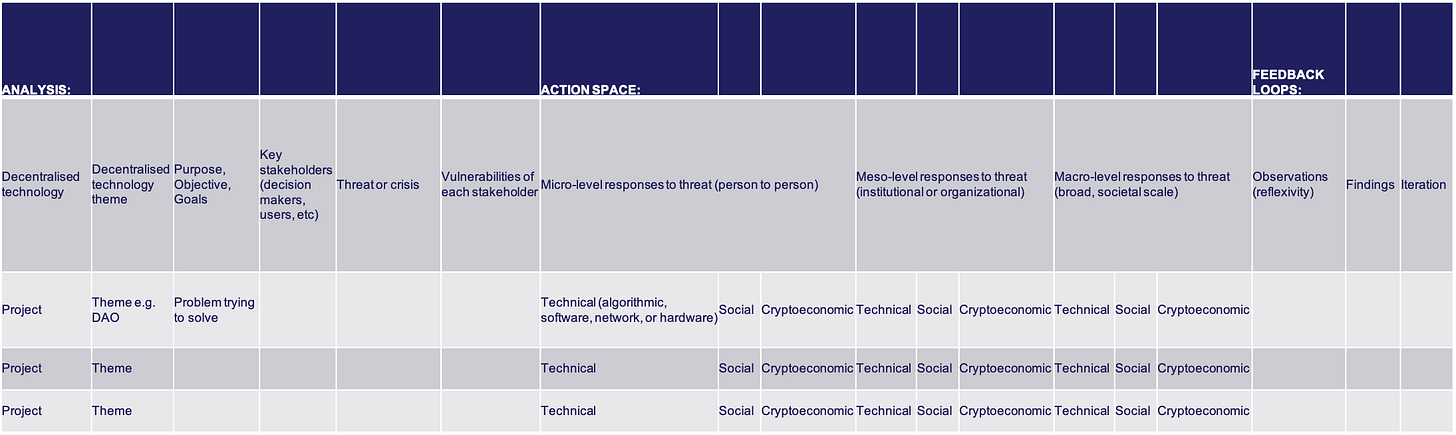
Below is a tool under development, for both observing resilience, and engaging in an action space of how to improve it. The framework offers a process by which to observe and govern vulnerabilities, as a means by which to afford adaptive capacity in decentralised technologies as socio-technical systems, to pursue greater resilience.
Figure 1: A model for observing resilience in socio-technical systems
Analysis:
The analysis involves choosing a project, identifying objective and goals of the project, the key stakeholders in as many dimensions of that project as possible, determining their threat models and identifying any crisis’ that stakeholders may be exposed to, and listing the vulnerabilities of each sub-set of stakeholders. “Threats” or crisis help reveal infrastructures, which “become visible upon breakdown”.[24]
An example is a community protocols vulnerability to sybil attacks.[25]
Action Space:
The action space introduces the processes and practices of “governing” vulnerabilities. Here, multiple scales are identified at which governance observations can take place among stakeholders. The action space can also be used as a design tool (where you become an participatory stakeholder), to identify where governance interventions can take place, by which to reduce or mitigate the vulnerabilities of certain stakeholders, against certain threats. This includes technical interventions, social interventions, or cryptoeconomic incentive-oriented interventions.
An example is a machine learning algorithm to flag potential sybil attacks.[26]
Feedback loops:
These steps formulate a feedback loops, to indicate the evolutionary nature of socio-technical systems, in that they are constantly adapting and changing, requiring ongoing analysis, governance, and iterations. Feedback loops are embedded in the observation and reflection (or reflexivity).[27] This practice of reflexivity surfaces findings, by which to hypothesise iterations at any scale or on any substrate of the infrastructure, to address certain goals.
As mentioned, this model can be utilised for both observation of what’s happening with regard to resilience in decentralised infrastructures, or for staging and testing governance interventions, in an attempt to enhance adaptive capacity and improve resilience in decentralised infrastructure.
Conclusion and next steps…
The aim of this approach towards a model of resilience in decentralised socio-technical infrastructure is to determine if vulnerabilities can be identified and “governed” in decentralized technologies, to afford adaptive capacity, towards more resilient digital infrastructure.
This resilience methodology is useful for analysis and design at numerous layers of the decentralised technology stack: from specific components such as anti-sybil decentralized identity mechanisms, to decentralized governance and organisation, to protocols, to decentralised applications. It is actively being applied in a number of projects in conjunction in valued industry research partnerships.
In the context of digital era, the adaptive capacity and resilience of digital infrastructure is hyper-relevant. Resilience exists within the social contexts and outcomes by which people use digital infrastructure. Paul Baran, inventor of distributed systems, refers to this pursuit of protecting end users as “the engineer’s responsibility”.[28]
- End.
[1] Baran. P. “On Distributed Communication Networks”. RAND Corporation. 1962. Available online: https://www.rand.org/pubs/papers/P2626.html. Accessed May, 2021.
[2] Diffie, Whitfield and Hellman, Martin, “New Directions in Cryptography”, IEEE Transactions on Information Theory, 22 (6: 1976), 644-654. Doi: 10.1.1.37.9720; Chaum, D. “Security without Identification, Card Computers to make Big Brother Obsolete”, Communications of the ACM, vol. 28 (10), 1985, pp. 1030-1044.
[3] May, T. The Crypto Anarchist Manifesto. Available online: https://www.activism.net/cypherpunk/crypto-anarchy.html. Accessed 15 Aug. 2020; Hughes, E. “A Cypherpunk’s Manifesto.” (1993) in The Electronic Privacy Papers: Documents on the Battle for Privacy in the Age of Surveillance, John Wiley & Sons, Inc. (1997), 285–87.
[4] Star, S. L., and Ruhleder, K. “Steps Toward an Ecology of Infrastructure: Design and Access for Large Information Spaces.” Information Systems Research 7 (1996): 111–34.
[5] I acknowledge that Bitcoin and blockchain are neither the “first” nor the “best” decentralised technology. Albeit scholars acknowledge its significance in the trajectory of decentralised technologies as an object of social enquiry, see: Karlstrom, H. “Do libertarians dream of electric coins? The material embeddedness of Bitcoin”. Distinktion: Journal of Social Theory 15, no. 1 (2014), 3, doi:10.1080/1600910x.2013.870083; Maurer, B., Nelms, T. C., Swartz, L. ‘“When perhaps the real problem is money itself!”: the practical materiality of Bitcoin’, Social Semiotics, doi: 10.1080/10350330.2013.777594, 2; Heemsbergen, Luke, A. Maddox, & R. Fordyce. “Blockchained to What (end)? A Socio-Material Provocation to Check Distributed Futures.” In Blockchain and Web 3.0, 1st Ed. (Routledge, 2020).
[6] Hayes, A. “The Socio-Technological Lives of Bitcoin.” Theory, Culture & Society 36, no. 4 (2019), 49. doi:10.1177/0263276419826218.
[7] Hanseth, O., and Monterio, E. “Understanding Information Infrastructure”, Manuscript, 1998. Available online: https://www.researchgate.net/publication/265066841_Understanding_Information_Infrastructure. Accessed March, 2021, 40-53.
[8] Nabben, K. & Zargham, M. “Permissionlessness: exploring a commonly misconceived and convoluted term”. Substack. 2021. Available online: https://kelsienabben.substack.com/p/permissionlessness-exploring-a-commonly. Accessed June, 2021.
[9] Nabben, K., & Zargham, M., “Resilience of the Commons: observing “resilience” in the governance of decentralised technology communities”, Substack, 2021. Available online: https://kelsienabben.substack.com/p/resilience-of-the-commons-observing. Accessed July, 2021.
[10] Hayes, A. “The Socio-Technological Lives of Bitcoin.” Theory, Culture & Society 36, no. 4 (2019), 49. doi:10.1177/0263276419826218.
[11] Voshmgir, S. and Zargham, M. “Foundations of Cryptoeconomic Systems”. Working Paper Series. Vienna University of Economics and Business. no. 1 (2019).
[12] Edwards, P, Bowker, G, Jackson, S, and Williams, R. “Introduction: An Agenda for Infrastructure Studies.” Journal of the Association for Information Systems, 10 (5, 2009). doi: 10.17705/1jais.00200, 369.
[13] Tantri, F. and Amir, S. “Modelling a Simulation for Sociotechnical Resilience.” Complexity, 1 (2019): 1-22, doi: 10.1155/2019/7950629.
[14] Nabben, K. (2021). “Blockchain Security as “People Security”: Applying Sociotechnical Security to Blockchain Technology”. Frontiers in Computer Science. doi: 10.3389/fcomp.2020.599406.
[15] Nabben, K., & Zargham, M., “Resilience of the Commons: observing “resilience” in the governance of decentralised technology communities”, Substack, 2021. Available online: https://kelsienabben.substack.com/p/resilience-of-the-commons-observing. Accessed July, 2021.
[16] Burchell, G., Gordon, C., Miller, P. (Eds.), The Foucault Effect: Studies in Governmentality with two lectures by and an interview with Michael Foucault, (Cambridge University Press: 2014).
[17] Burchell, et. al., The Foucault Effect;Nabben, K, Bernholz, L, Allen, A., Poblet, M. “Blockchain and Assembly: An Exploration”, Substack. 2021. Available online: https://kelsienabben.substack.com/p/blockchain-and-assembly-an-exploration. Accessed July, 2021.
[18] Edwards, P, Bowker, G, Jackson, S, and Williams, R. “Introduction: An Agenda for Infrastructure Studies.” Journal of the Association for Information Systems, 10 (5, 2009). doi: 10.17705/1jais.00200, 373.
[19] Healy, S., & Mesman, J. "Resilience: Contingency, Complexity, and Practice," in in Hommels., A., Mesman, J, Bijker, W.E., (eds). Vulnerability in Technological Cultures: New Directions in Research and Governance, MIT Press (2014). 155-177.
[20] Hommels., A., Mesman, J, Bijker, W.E, "Framing the Vulnerability Issue," in Vulnerability in Technological Cultures: New Directions in Research and Governance , MIT Press, 2014, pp.27-31.
[21] Boyd, S. and Vandenberghe, L. Convex Optimization. (Cambridge University Press: 2004).
[22] Hommels., A., Mesman, J, Bijker, W.E. "The Governance of Vulnerability," in Vulnerability in Technological Cultures: New Directions in Research and Governance, MIT Press (2014). 217-222.
[23] Nabben, K. “A Provocation on Privacy & Ethics in Blockchain-Based Systems: An Invitation”, SSRN, (2021). Doi: 10.2139/ssrn.3834290
[24] Star, S. L., and Ruhleder, K. “Steps Toward an Ecology of Infrastructure: Design and Access for Large Information Spaces.” Information Systems Research 7 (1996): 111.
[25] Nabben, K., & Zargham, M., “Resilience of the Commons: observing “resilience” in the governance of decentralised technology communities”, Substack, 2021. Available online: https://kelsienabben.substack.com/p/resilience-of-the-commons-observing. Accessed July, 2021.
[26] Emmett, J., Nabben, K., Bernardineli, D.L., Zargham, M. “Deterring Adversarial Behavior at Scale in Gitcoin Grants: A Framework for Community-Based Algorithmic Policy Making”. Medium. Available online: https://medium.com/block-science/deterring-adversarial-behavior-at-scale-in-gitcoin-grants-a8a5cd7899ff. Accessed 2 June, 2021.
[27] Nabben, K, & Zargham, M. “Techno-reflexivity: a creative methodology for software developer un-bias”, Substack, 2021. Available online: https://kelsienabben.substack.com/p/techno-reflexivity-cf1331278bdc. Accessed July, 2021.
[28] Baran, P. “On the Engineer’s Responsibility in Protecting Privacy”. RAND Corporation. 1968. Doi: 10.7249/P3829.
Acknowledgments:
With thanks to the team at Blockscience for ongoing intellectual engagement on these research themes, as well as my PhD supervisors at RMIT University.